
RSA NetWitness Logs
SIEM Log Management
Sorry, this product is no longer available, please contact us for a replacement.
Click here to jump to more pricing!
Overview:
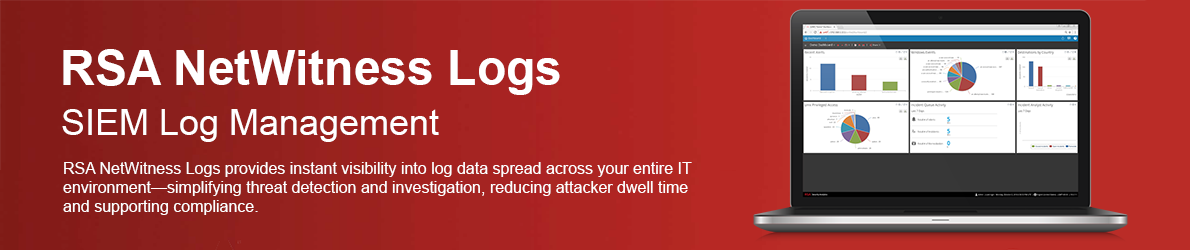
RSA NetWitness Logs provides instant visibility into log data spread across your entire IT environment—simplifying threat detection and investigation, reducing attacker dwell time and supporting compliance. It allows you to:
- Centrally manage logs no matter how complex your architecture
- Monitor logs generated by public clouds and SaaS applications
- Identify suspicious activity that evades signature-based security tools
- Gain instant log visibility via "dynamic parsing" technology
The Role of Log Management and Monitoring in Security
Log management and monitoring tools have long played an indispensable role in cybersecurity. Since every application, system, server and endpoint in an organization generates logs, or records of activity, security teams look to them to identify potential indicators of compromise. But since organizations generate so many logs in so many different formats, collecting, storing and analyzing this data has long been a challenge—one that is growing more daunting with cloud adoption.
Log management and monitoring tools like RSA NetWitness Logs are designed to address those challenges by collecting data from a wide range of sources (both on premises and in the cloud), interpreting relevant security information from this data, providing short- and longer-term retention capabilities, and applying advanced analytics to speed correlation and detection.
Features:
![]()
Patented Parsing and Indexing Technology
Dynamically parses and enriches log data at capture time, creating sessionized metadata that dramatically accelerates alerting and analysis. This patented technology is a key differentiator of the product.
![]()
User and Entity Behavior Analytics (UEBA)
UEBA capabilities automatically detect command and control (C2) communications, lateral movement and other suspicious activities that evade signature-based tools. Visibility combined with analytics gives security teams opportunities to stop attackers before they achieve their objectives.
![]()
Log Management and Monitoring
Ingests logs from more than 350 event sources; monitors public clouds such as AWS and Azure and SaaS applications including Office 365 and Salesforce.com; and interprets relevant security information from a wide range of protocols including Syslog, ODBC, SFTP, SCP, FTPS and many more.
![]()
Endpoint Visibility
A purpose-built agent offers context, essential endpoint inventory scans and a capability for easily forwarding Windows logs.
![]()
Compliance Support
Includes use cases and pre-built templates for compliance with a range of regulations, including Sarbanes-Oxley, PCI-DSS, HIPAA, NERC and many others.
![]()
Reporting
Provides the flexibility to customize views and formatting for reports. Predefined reports comprise one or more rules that you can also leverage within other custom-built reports.
Benefits:
Simplifies Monitoring of Windows Logs
A purpose-built agent offers endpoint inventory scans and provides Microsoft Windows log forwarding and filtering capabilities to simplify the monitoring of Windows logs and reduce the cost and complexity of investigating threats.
Alleviates Analysts’ Alert Fatigue
RSA NetWitness Logs enriches log data with threat intelligence and contextual information (about user identities, for example) to quickly identify high-priority threats and reduce false positives.
Meets Rigorous Security Requirements
RSA NetWitness Logs received the Common Criteria certification for product security and is certified for U.S. Department of Defense Information Network UC APL.
Brings Relief to Understaffed Security Teams
Connects incidents over time to expose the full scope of an attack and provides analysts with orchestration and automation The RSA NetWitness Logs discovery workflow eases the challenges associated with monitoring diverse, dynamic IT environments where new log sources frequently come online. It does not require manual configuration and includes an automated parsing tool that helps security teams rapidly ingest new log sources.
Speeds Threat Detection and Investigation
By providing immediate, pervasive visibility into all relevant sources of log data and by dynamically parsing and enriching this data at capture time to create sessionized metadata, RSA NetWitness Logs dramatically accelerates alerting and analysis to speed detection and investigation.
Centrally Manages and Monitors Logs
Because you can deploy log collection components on-premises, virtually, across hybrid architectures, and within public clouds and SaaS applications, RSA NetWitness Logs provides a platform for centrally managing and monitoring logs no matter their source and no matter how complicated your IT architecture.
Documentation:
Download the RSA NetWitness Logs Datasheet (.PDF)
Pricing Notes:
- Pricing and product availability subject to change without notice.

